 As we continue the journey into Linux Security for the LPIC-3 303 exam we look at how we can adjust Kernel settings to block network pings being responded to from the Linux server. Many simple attacks will start with a ping sweep of your network. We the complete subnet is pinged. Servers that respond to the ping can then be further examined for services to exploit. Even though it does not stop your services from being discovered disabling PING responses from your server will help obscure it. Security is a many faceted approach and each method implemented adds to the value of your security approach. We will look at disabling ICMP packets on the server using the procfs. In the Network Security course we will also see how we can use a firewall to block ICMP packets to the server.
As we continue the journey into Linux Security for the LPIC-3 303 exam we look at how we can adjust Kernel settings to block network pings being responded to from the Linux server. Many simple attacks will start with a ping sweep of your network. We the complete subnet is pinged. Servers that respond to the ping can then be further examined for services to exploit. Even though it does not stop your services from being discovered disabling PING responses from your server will help obscure it. Security is a many faceted approach and each method implemented adds to the value of your security approach. We will look at disabling ICMP packets on the server using the procfs. In the Network Security course we will also see how we can use a firewall to block ICMP packets to the server.
By blocking ICMP responses from the server we also effectively stop us using the server to ping other devices as we can ping the remote device but we are unable to read the ping response.
Each objective is available to view online. However if you prefer to have all the content in one place and study from an eBook then the objective ‘LPIC 3 Linux Security 326.1 Host Hardening’ is now available to download for just £0.99.
Block Network Pings or ICMP Echo Resonses
$ sysctl -ar 'icmp_echo' net.ipv4.icmp_echo_ignore_all = 0 net.ipv4.icmp_echo_ignore_broadcasts = 1
By default, we do not respond to ICMP broadcasts which is a good thing, to obscure the server further we will prevent response to directed pings also.
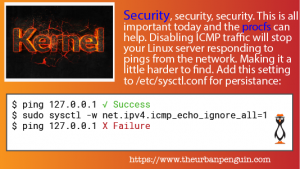
$ sudo sysctl -w net.ipv4.icmp_echo_ignore_all=1 net.ipv4.icmp_echo_ignore_all = 1
We now no longer respond to pings
$ ping -c3 localhost PING localhost (127.0.0.1) 56(84) bytes of data. --- localhost ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 1999ms
To persist this setting, as always we would need to add this to the sysctl.conf or included file from the /etc/sysctl.d/ directory.
The video follows:
