[custom-header-login]
| Weight | 2 |
| Description | Candidates should be able to install and configure a proxy server, including access policies, authentication and resource usage. |
Key Knowledge Areas:
- Squid 3.x configuration files, terms and utilities
- Access restriction methods
- Client user authentication methods
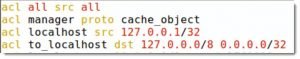
- Layout and content of ACL in the Squid configuration files
The following is a partial list of the used files, terms and utilities:
- squid.conf
- acl
- http_access