- Weight: 4
- Description: Candidates should know how to use GPG. This includes key generation, signing and publishing to keyservers. Managing multiple private key and IDs is also included.
Key Knowledge Areas
- GPG encyption and signing
- private/public key management
- GPG key servers
- GPG configuration
Terms and Utilities
- gpg
- gpgv
- gpg-agent
- ~/.gnupg/
I am certain that we have used GPG, Gnu Privacy Guard before but many courses stop at the basics of generating, exporting and importing keys, and whilst you may say that it is important the burning question is always about easier distribution of keys. John and Alice have to find a more convenient way to exchange keys or their tryst is not going to last. The LPI and with LPIC-3 and the exam 303 differentiates itself in looking at more advanced topics whilst making sure the basics are still covered. In this tutorial we look at establishing our own key-server, perhaps a corporate key-server to ease key exchange within the company. With the key-server in place we can look a little more at the gpg commands and configuration.
Installing the SKS Key-Server on Ubuntu 12.04 Server
GPG key-servers allow for public keys to be stored easily to be searched and imported as needed by anyone that needs to securely send information to the recipient and owner of the public key. By the very term public these keys should be in the public domain and easily accessible.
Public servers do exist and include:
- https://sks-keyservers.net
- http://keyserver.ubuntu.com
- http://keyserver.oeg.com.au
There is need to install your own server, but for completeness, we will. Public Key servers generally will synchronize with each other (SKS = Synchronizing Key server) so use of any server should suffice but you may want your own server for testing or as a private server for internal function only.
For ease we will install on Ubuntu 12.04 LTS server as the SKS package is part of the standard repositories and makes for a simple and quick install.
sudo apt-get update sudo apt-get install sks
Once installed you may review the man page:
man sks
Now we can build the database for sks using the command sks(/usr/sbin/sks)
sks build
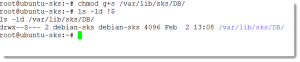
We will also need to set the permissions correctly. The account you use will be debian-sks for both the user and the group. We can check the account names using grep to search the /etc/passwd and /etc/group files:
grep debian-sks /etc/{passwd,group}
Now we are certain on the correct names we can use chown to set the ownership correctly, setting the SGID bit on the directory will ensure all new files in the DB directory are correctly group owned by debian-sks :
chown -R debian-sks:debian-sks /var/lib/sks/DB chmod g+s /var/lib/sks/DB
To ensure that the sks service is started at boot we must edit the file /etc/default/sks. The line initstart should be set to yes if you would like the service started on boot.
Now we can start the service manually using:
/etc/init.d/sks start
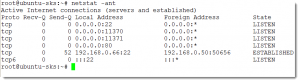
Using netstat we can confirm that the service listening on TCP ports 11370 and 11371
- 11370 : Is used for synchronizing with other keyservers
- 11371 : Is used for http requests and client connection from gpg
netstat -ant
Keys can be sent to the server with:
gpg --keyserver <address of server> --send-key <key id>
Keys can be search and imported from the server with
gpg --keyserver <address of server> --search-key <string>
Or you can add a web front end to the SKS server by adding an index.html page to the directory /var/lib/sks/www.