Oracle Solaris 11 has a security mechanism within RBAC that goes beyond the normal OS security we may expect to find. We may want a user account to be able to back-up the complete file-system for this they will need to be able to read all files. It is a mammoth task to ensure the user has read access to all files so often the root account may be used for this. Using privileges within RBAC we can assign the user file_dac_read which allows them to read files even though they may not be in the files ACL. Now we maintain the security that we need using the concept of Least Privilege
Backup Operator
You may wish to configure specific rights for a user or service, historically; we have used the root account for many services or tasks as it was simply the only way or at least the easiest. If we needed an account to back-up the file-system then the account must be included in the ACL or mode of all files with the read permission. Practically this is difficult to maintain and again illustrates why root sometimes is used.
Using privileges in Oracle Solaris 11 can help with a more effective and secure solution. Assigning the file_dac_read privilege to a user or role then they can still read the file event though they may not be listed in the file’s ACL
Determine the privileges associated with an account
From the shell of the logged in user we can use the command
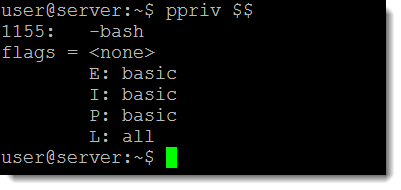
ppriv $$
The key here in the output shown in the following screenshot is the letter E for Effective:
Find out what privileges are needed
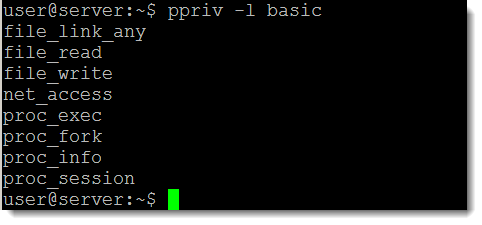
We have seen that the user has effective privileges set to basic when running the bash shell; we can list those privileges with the command:
ppriv -l basic
or
ppriv -lv basic
Adding the verbose option (-v) display information about the privilege. We can see that the basic privileges include file_read but this is only effective if the user already has the read permission to the file. To read from a file where we do not have permission we need file_dac_read. We can test this with the debug option to ppriv:
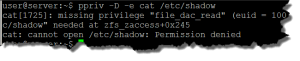
ppriv -D -e cat /etc/shadow
The output confirms we need file_dac_read to read from a file where we do not have the permissions within the ACL of the file.
Assign the privilege
Using usermod we can modify an existing users default privileges:
usermod -K defaultpriv=basic,file_dac_read user
or those for a new account
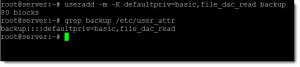
useradd -m -K defaultpriv=basic,file_dac_read backup
The privileges are stored in the file /etc/user_attr. In the following screen shot we see a new user created with the assigned privilege and then we search for the user in the user_attr file to display the persistent settings.
Once the password is assigned to the user we can log in and view the new privileges
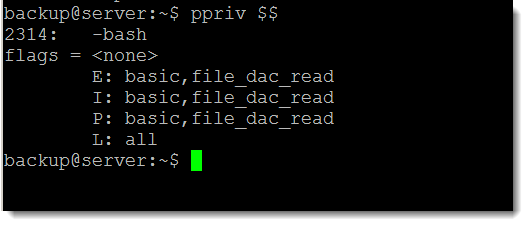
ppriv $$
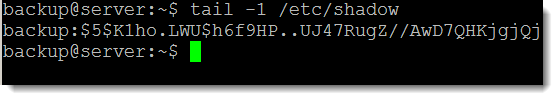
We can now see that the Effective privileges are set to basic and the file_dac_read. In this way we can now access files such as /etc/shadow that we do not read permissions to and as this is set for the server it easier than maintaining across each file in the file-system. Using the following command we can now see that we can read the /etc/shadow file as the backup user:
tail -1 /etc/shadow
Summary
Using a combination of file permissions set both on executable and regular files with privileges we can effectively maintain a secure structure on our Oracle Solaris 11 server or desktop.